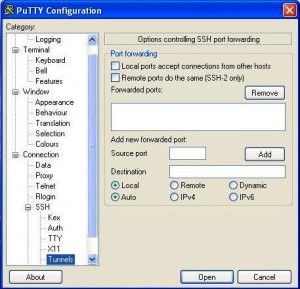
Of Hacks & Keyloggers…!!! “I don’t know what happened!; I don’t remember visiting any dodgy websites, downloading any weird apps, opening any suspicious emails or attachments, let alone links!, why I am receiving these sms & email notifications from my Bank!?!?” Sounds familiar right? Come to think of it, in most cases the unsuspecting victim is being honest. That being said, I just remembered something; a previous write up revolving around one of the methods used to carry out this type of attack. It can happen to anyone, in fact I was once a victim!
Of Hacks & Keyloggers…!!! “I don’t know what happened!; I don’t remember visiting any dodgy websites, downloading any weird apps, opening any suspicious emails or attachments, let alone links!, why I am receiving these sms & email notifications from my Bank!?!?” Sounds familiar right? Come to think of it, in most cases the unsuspecting victim is being honest. That being said, I just remembered something; a previous write up revolving around one of the methods used to carry out this type of attack. It can happen to anyone, in fact I was once a victim!
What is a keylogger?